Bluetooth® Mesh Basics
Centralized vs. Distributed
“Centralized” networks allow a central device to talk with many peripheral devices. Also called a “star” system because of the geometry. In a centralized system, most of the computing power and resources reside inside the main point. Example: a mainframe computer and terminals.
In a “decentralized” network, the central device is split in several or many ones which are then connected together and communicate to the peripheral devices. Example: PCs connected with ethernet cable within an office and to a cloud server outside the office.

Nodes
A device is called a “node” in Bluetooth® Mesh as it is node on a network.
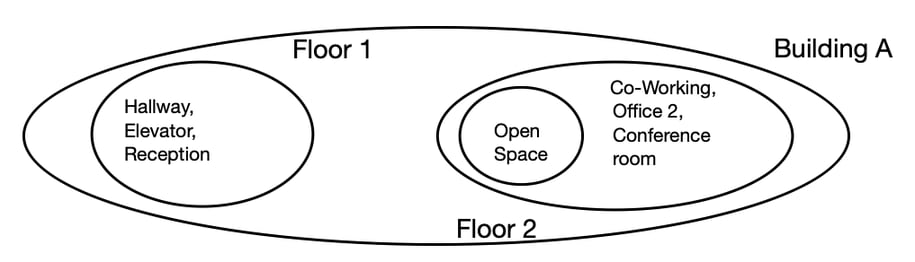
Groups
Groups define the topography of the network. Groups can nest inside a group. For simplification, groups cannot intersect, unless rule is overwritten at PRO level. There can be up to 16 levels of groups inside a group. There can be up to 16,383 unique groups within a network.
Publish/Subscribe
In Bluetooth® Mesh, assigning a node to a group is properly called “subscribing” a node to a group. This means that every message sent from the network to the group is received by the subscribed node.
Publishing is the technical term for the communication from the node to the group. Nodes do not communicate to each other, they subscribe and publish to groups.

Relay
Messages get sent from nodes to other nodes that are in direct radio range of the publishing node. Nodes can act as “relays” and retransmit messages so that they can travel further, in a number of “hops”. Hop time is between 2ms. and 15 ms. depending on the traffic on the network. For small network, by default, all nodes are relays. For large networks, traffic is managed by turning relays ON and OFF in strategic places. This tuning of the network is available only at PRO level.
Bluetooth® Mesh is a very reliable network because of its multi-hop and multi-path architecture

Proxy - Pro Level
A “proxy” node can communicate Bluetooth® Mesh and Bluetooth® Low Energy; Bluetooth® Low Energy is the Bluetooth® standard used at the moment by most consumer products such as smartphones and tablets (Bluetooth® Low Energy is a point-to-point standard while Bluetooth® Mesh is a many-to-many standard). Bluetooth® Low Energy devices can communicate with a mesh network via a proxy node. In this way a smartphone can monitor and control a Bluetooth® Mesh Network. By default, when a network is commissioned, the first 10 nodes are proxy and the subsequent nodes are proxy 1 out of 5. This standard configuration can be modified at PRO level only.
Low Power Node (LPN)
In order for a device to run Mesh on small battery or on energy harvesting, the device should be able to suspend the radio and enter deep sleep mode, it should be able to send a few bytes of data over a period of time without receiving or relaying other messages and it should be able to communicate with the network immediately after wakeup. This is a “LPN” configuration.
Friend - Pro Level
A Friend is a node which stores messages addressed to LPNs they are friends with and forward them when the LPN occasionally wakes up and polls. Friendship is an automated feature. At PRO level, nodes friendship can be enabled or disabled.

Commissioning
The “commissioning” of a network is divided into two operations: Provisioning and Configuration.
Provisioning is the security process by which a network is created and/or a device joins as a member of the network. Only members of the same network can talk to each other. Configuration is process of defining the sequence of operations of the network. This includes groups, schedules, scenes and so much more.

Proxy - Pro Level
In Bluetooth® Mesh, security is mandatory. All messages are encrypted and authenticated. Network keys are generated when the network is created during provisioning. Without network key a node or provisioner (such a smartphone + app) cannot communicate with the network.
App Keys - Pro Level
An App Key is an encryption key which is bounded to a network key, provided to nodes after provisioning with the function of further securing specific applications (also called “models”). App Keys are bounded to one or more models. This allows for instance to separate applications such as lighting, audio and video and authorize users to access to certain applications only.